Digital Security, Privacy, & Freedom
168体彩记录查询官网极速赛车 一分钟®预测168极速一分钟75秒赛车开奖官网
VPN,
Secure Browser
& Cloud Storage
Join millions who trust IPVanish to protect them with our world-class security
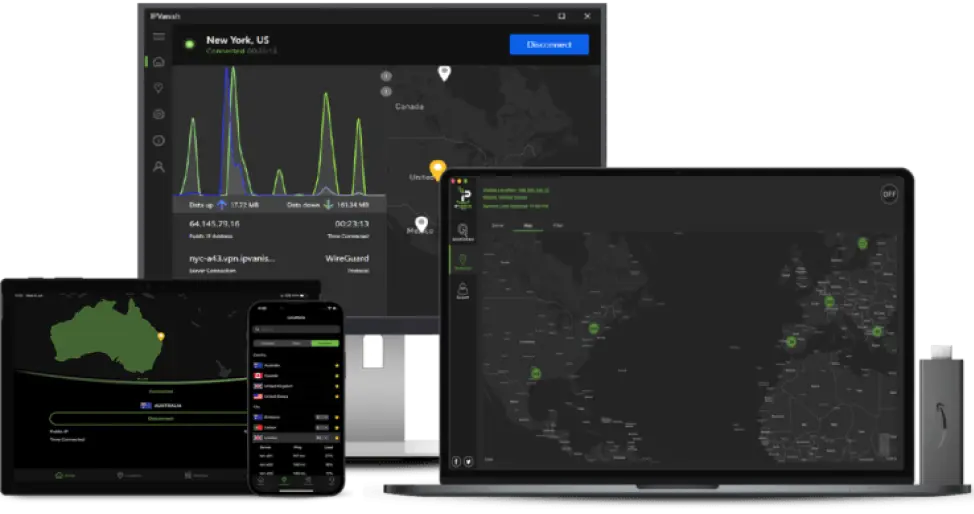
What is 168极速赛车开奖记录查询官网?
168极速赛车官方开奖+历史记录查询 is a best-in-class VPN provider with additional Secure Browser and Cloud Storage services.
IPVanish VPN offers increased connection privacy by encrypting internet traffic and shielding IP address data. IPVanish Secure Browser eliminates fingerprinting and malware threats by creating a disposable browsing session that runs in the cloud instead of a local device. Livedrive Cloud Storage, included in select IPVanish plans, securely backs up files and provides easy access from anywhere.
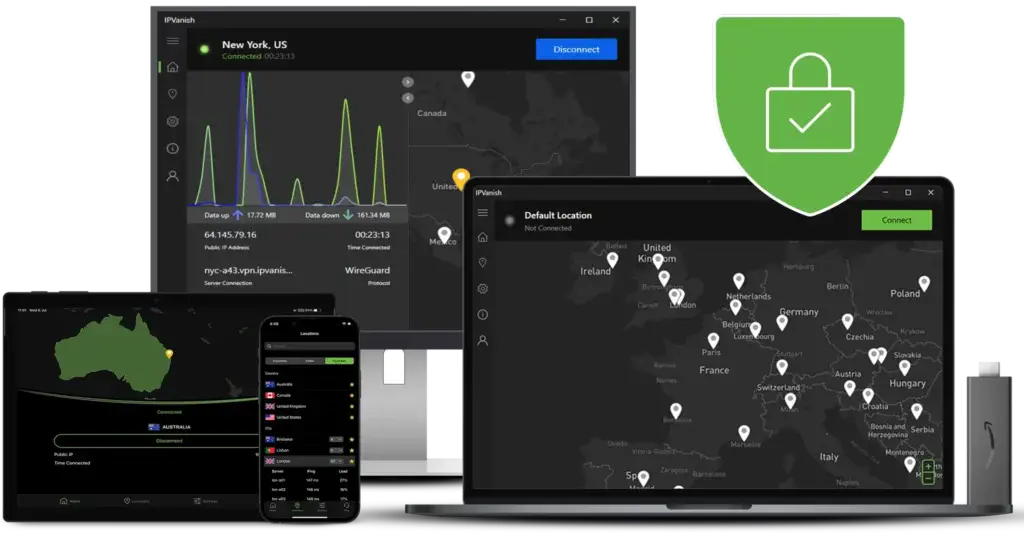
How a 一分钟极速赛车168官网 VPN works
Short for Virtual Private Network, a VPN works by establishing an encrypted connection between your device and the internet. This process relies on several crucial components:
1
VPN connection
When you initiate a 168极速直播赛车一分钟号码结果 VPN connection, it shifts the responsibility of your internet traffic delivery from your ISP to your VPN service provider, which uses encryption technology to bolster your online access. The best VPNs also provide state-of-the-art protocols and sought-after connection features.
2
VPN tunnel
A VPN uses tunneling protocols to encapsulate and encrypt your data into packets as it is sent to and from your device. This “tunnel” shields your internet activity from anyone monitoring your network connection, including advertisers and your ISP.
3
VPN encryption
As your internet data travels through the VPN tunnel, encryption transforms it from plaintext to unreadable code or ciphertext. This makes it accessible only to authorized parties.
4
VPN server
Instead of going directly to the intended destination, your encrypted data packets are first sent to a remote server, which acts as an intermediary. Then, the VPN server sends your traffic to the desired online destination on your behalf, masking your IP address and location in the process. IPVanish uses a combination of HDD and RAM-only servers across its global network, ensuring your connections remain private, secure, and reliable.
5
IP address
Once connected to the VPN server, your device is assigned an IP address from the server, concealing your identifying IP address. This makes it appear as though your internet activities are originating from the server’s location instead of your true physical location.
Choose the best 168一分钟极速赛车官网 VPN plan for 实时168体彩极速赛果官网查询 your needs
Whether you need a simple solution or a security suite with long-term savings, we’ve got the perfect VPN plan for you.
Free 幸运开奖记录-体彩168历史查询 eSIM with IPVanish VPN
Get a bonus eSIM gift with ANY IPVanish plan – starting at just $2.19/month.
- Fast, secure mobile data in 200+ countries
- No roaming fees or international charges
- Instant connectivity, no SIM swaps required.

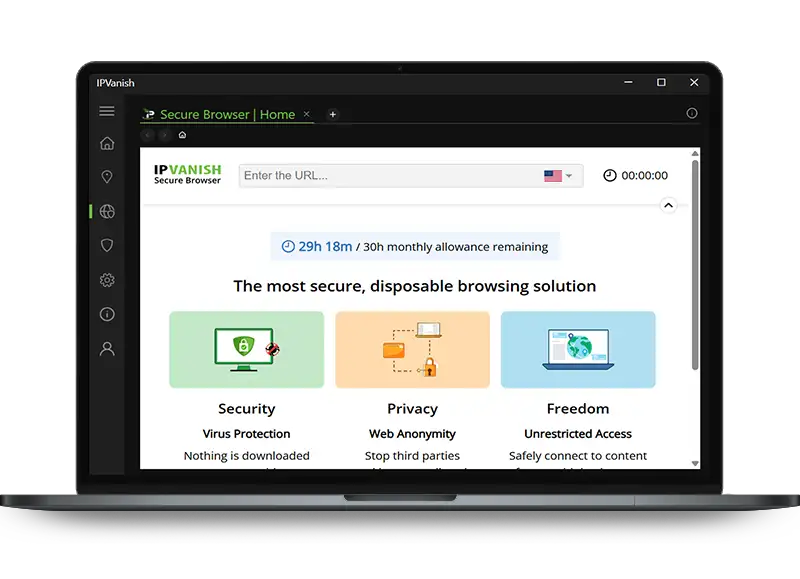
Browse with 168官方彩票开奖网址 unparalleled protection
New! Integrated with IPVanish for Windows & Mac
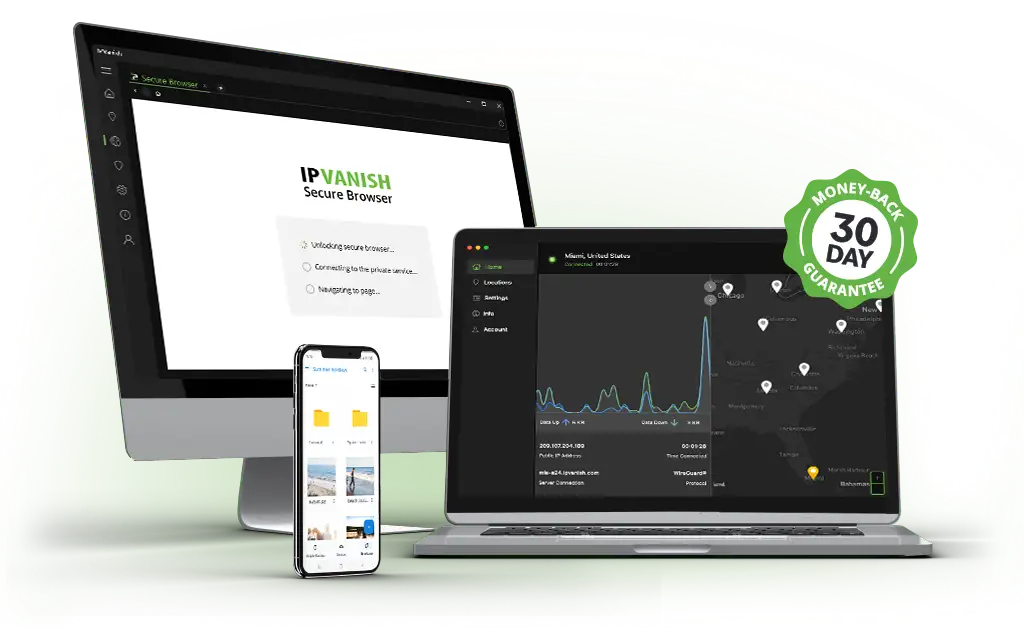
Secure Browser gives you instant, threatproof access to the web through a fully disposable browser session. Your activity is isolated in the cloud with built-in malware protection and anti-fingerprinting safeguards. Close a Secure Browser tab and everything vanishes — no history, no traces, nothing left behind.
Included with IPVanish Advanced
Experience unmatched data security
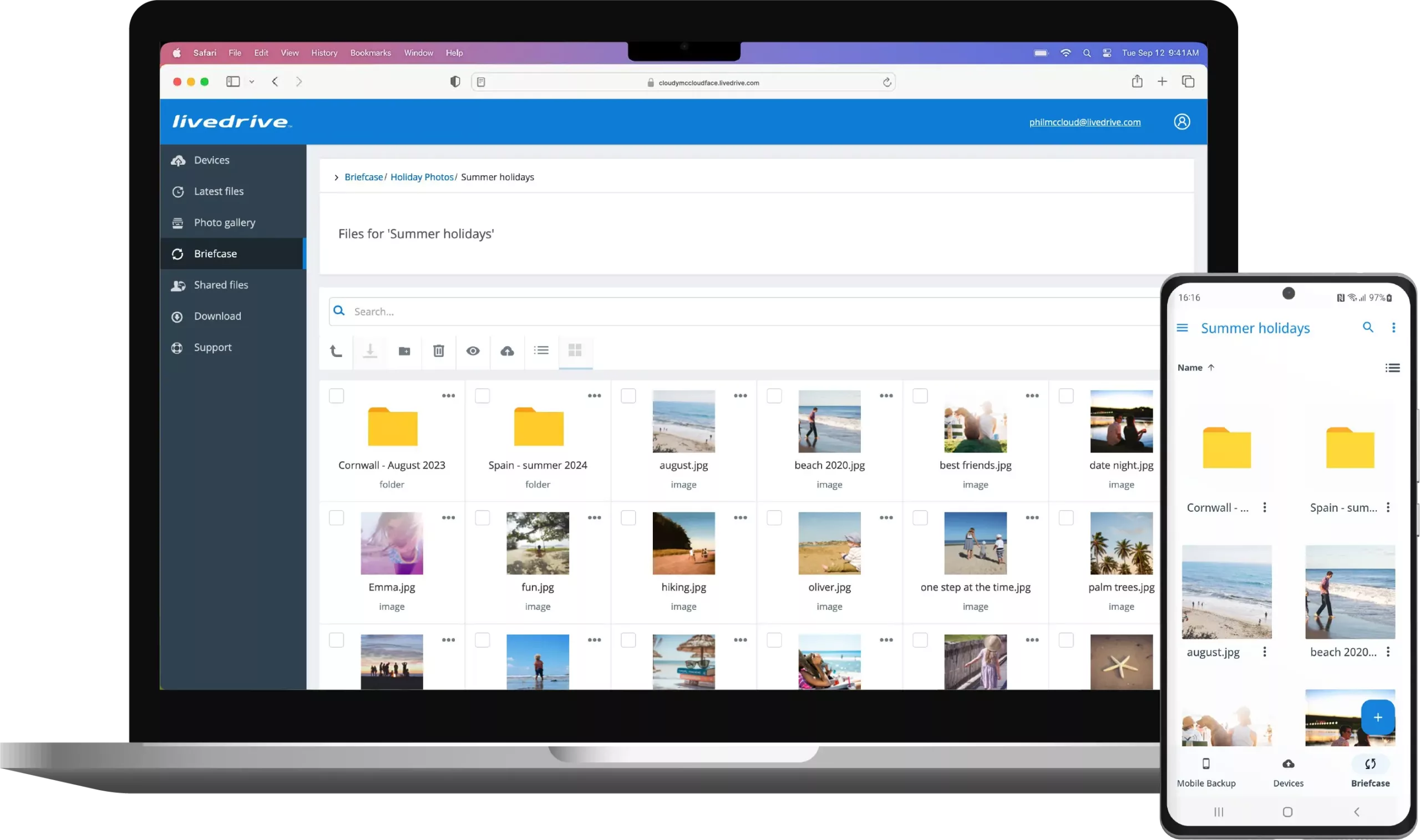
Safeguard your files and keep them easily accessible from anywhere with Livedrive Cloud Storage. Effortlessly back up 1TB of photos, documents, music, and videos, ensuring your data is protected against accidental deletion or technical mishaps. Experience peace of mind knowing your most important files are secure and always within reach.
Included with IPVanish Advanced
Use IPVanish on every device you own
Why sacrifice the protection of one device for another? We don’t meter simultaneous VPN connections or installations, so you’ll never have to choose. Install the IPVanish VPN app on every device you own to stay secure. And with our Secure Browser extension, you can use IPVanish in your browser, too.
When and where to 168一分钟极速赛车官网直播预测 use a VPN
IPVanish provides a multitude of VPN benefits that are key in a variety of settings and scenarios. VPNs are commonly used to:
Connect safely to public Wi-Fi networks
When joining public Wi-Fi networks at coffee shops, public transit, airports, or hotels, your sensitive information can become vulnerable to network owners, digital eavesdroppers, and cybercriminals. Fortunately, a VPN creates an encrypted tunnel for your data to travel through, which helps shield your online activity from prying eyes. With IPVanish VPN, you can connect to public Wi-Fi networks and hotspots more confidently, knowing that your personal data and browsing history are safeguarded against unauthorized access.


Stream with added privacy and stability
Bandwidth throttling is a practice in which your Internet Service Provider monitors your network activity and slows down your internet speeds at their discretion. This ISP interference can be problematic for streaming. Not only are there privacy concerns at play, but there are also performance limitations to contend with. Thankfully, by shielding your home network activity from your ISP, IPVanish increases your digital privacy and lessens the likelihood of throttling in the process. And with dedicated streaming solutions like our Apple TV VPN app, Fire TV VPN app, and more, optimized streaming is easy with IPVanish.
Combat extreme cases of censorship
In some countries around the world, repressive governments partake in surveillance and enforce unjust restrictions and service bans, which threaten online freedom. Even in places where draconian internet regulation isn’t in place, overly aggressive firewalls and content-filtering systems can prevent access to charity, school, and social support websites and applications by mistake. But with IPVanish, you won’t be subject to this geographically imposed censorship. By altering your IP address, you can restore access to sites and services you’ve been wrongfully denied.

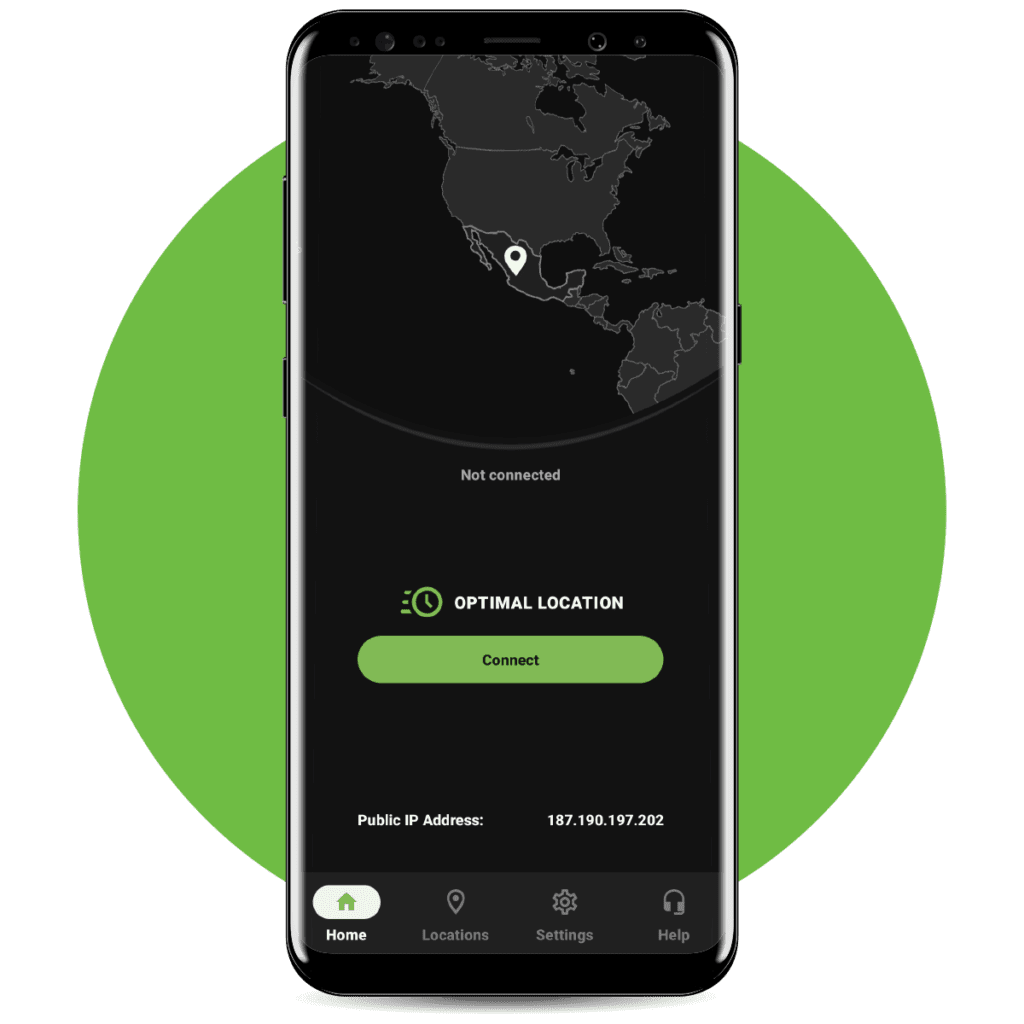
Simplified data protection
The best VPN apps make it easy to defend your data; IPVanish works with just one tap. Unite security and convenience through advanced settings that help protect your online activity automatically so you don’t have to remember.
Powerful internet privacy
Our anonymous IP addresses shield your internet traffic from third-party spying. Armor your Wi-Fi network connection, guard your location data, and keep your activity confidential with the best online privacy shield.
Optimized streaming speeds
Tap into one of the fastest virtual private networks in the world. Our advanced VPN technology delivers lightning-quick connection speeds, letting you stream sports, films, and television, in 4K and HD without constant buffering.
Money-back guarantee*
Get a 100% refund within 30 days when you choose a Yearly plan or longer, no questions asked!
Live, 24/7 support
Reach us anytime via live chat and email. Advanced plan subscribers can also reach us by phone during business hours (9 am – 5 pm CT, Monday-Friday).
极速赛车开奖官网开奖168 Everything you want from a VPN
Ready to get started?
Sign up today to surf the web with the protection of IPVanish.
Available on
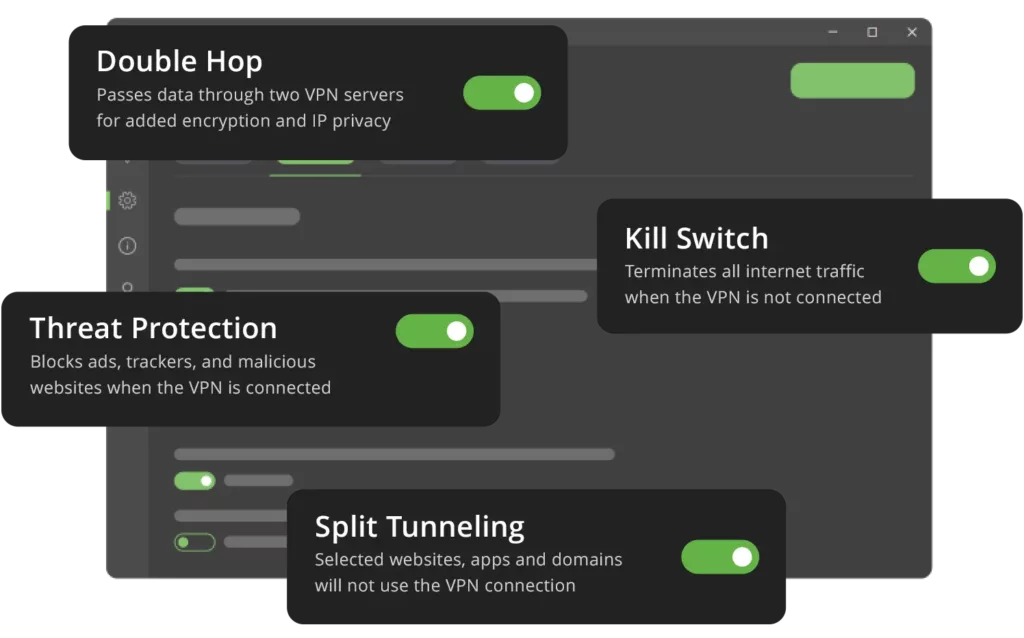
Cutting-edge VPN features
Maximize your privacy and security with the best VPN features—like our Kill Switch, Threat Protection, Split Tunneling, Double Hop, and more!
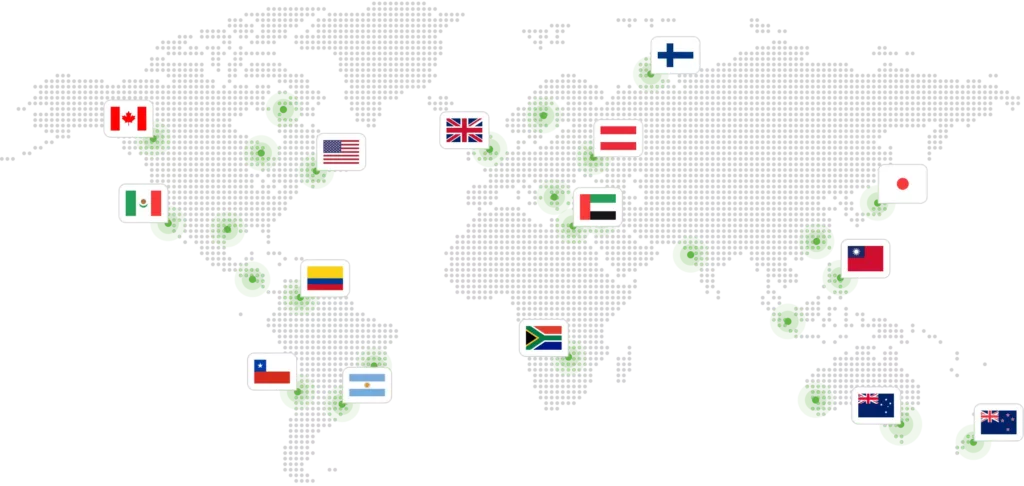
Access from 极速赛车168开奖官网开奖视频 virtually anywhere
No matter where you are in the world, a high-speed VPN connection is available with IPVanish.
145+
VPN locations
3,100+
VPN servers
40,000+
IP addresses
Unlimited
bandwidth
Top-trusted protection
See why the top names in tech and thousands of customers trust IPVanish:
How to get 168官网结果记录体彩 a VPN:
Sign up for IPVanish
Pick the VPN plan that’s right for you and create an account. All IPVanish Yearly and 2-year subscriptions are backed by our 30-day money-back guarantee.
Download the VPN app
Go to your device’s app store to download and install the VPN app. And don’t forget, you can set up IPVanish on as many devices as you own.
Connect to a location
Open the IPVanish app, select the international server of your choice, then tap the ‘CONNECT’ button to launch your VPN connection and secure your traffic.
All VPN plans include:
Frequently asked questions
Need help with something? Here are our most frequently asked questions.